How to read Wireshark capture: Everything you Should know
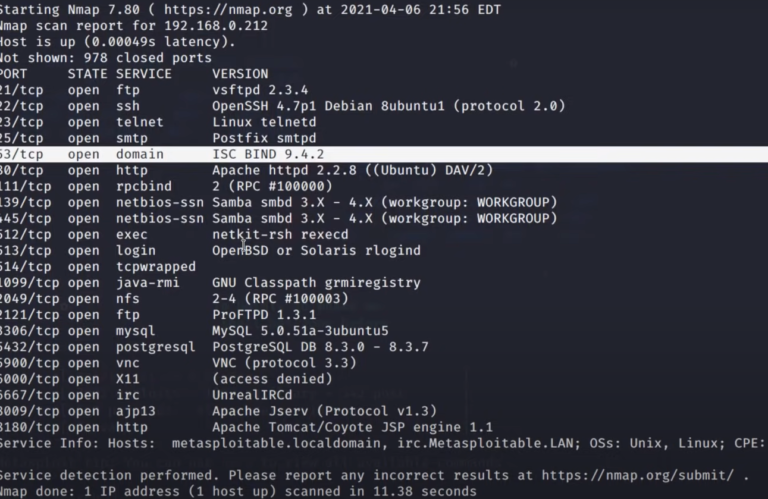
Master the art of network analysis with our guide on how to read Wireshark capture files. Unlock insights from your data today! What is Wireshark? Wireshark is an open-source packet analyzer that provides a graphical interface for How to read Wireshark capture and analyzing network traffic. It supports hundreds of protocols and can be used…