explain brute force attack Real-Life Examples
“Explore real-life examples to explain brute force attack its methods, and how it can compromise security. Understand the risks and how to protect against it.”
What is a Brute Force Attack?
A brute force attack is a method of attempting to gain unauthorized access to a system, network, or account by systematically guessing all possible combinations of passwords or encryption keys until the correct one is found. The name “brute force” refers to the attacker’s use of raw computational power to “brute force” their way through security.
How Brute Force Attacks Work
explain brute force attack are typically automated, meaning attackers use software tools to guess passwords or encryption keys at an incredibly fast rate. These tools can try thousands, even millions, of combinations per second, depending on the computational power of the attacker’s systems. The longer the password or encryption key, the more time and resources it takes to crack it.
explain brute force attack-how attacker get Password
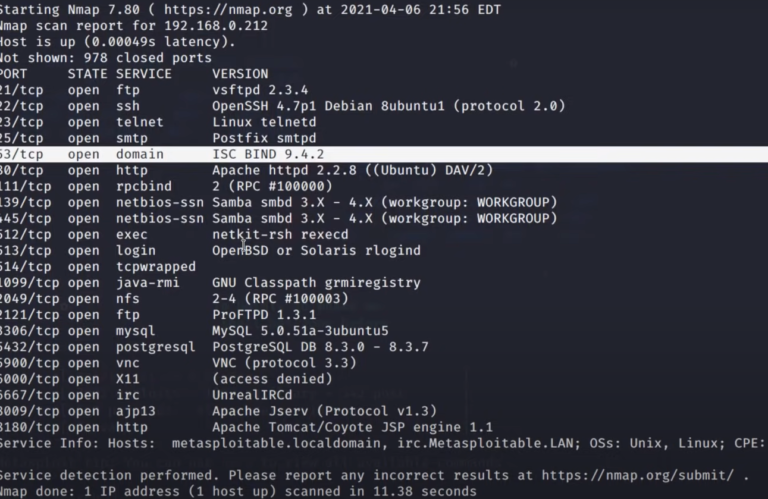
Let understand a real life examples in now days everyone use social media like Facebook instagram , twitter etc.
when you log in your social media account suppose you log in your Instagram by using your credentials ID and password.

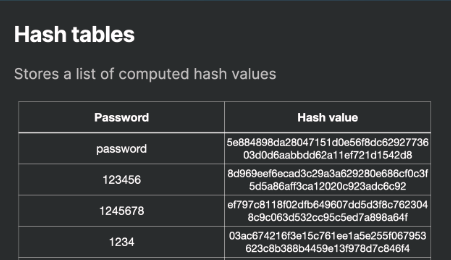
and you clearly see that the password is in *************** this user ID password store on the server but the password is changed into hash form by the help of hash algorithm .
hash algorithm is a method convert a input message by mathematical function to convert into a string size like 43434fdffjd4344345nj5nj4n343n4n43j5465l64l534l243n33b.
if a hacker or attacker hacked the server by his skill to get the database of the server and find the user information but the password is in hash form .he convert hash password into normal text by help of many tools.
- Rainbow Table:
- The key concept behind a rainbow table is to reduce the time needed to perform a brute force attack by trading off storage space. Here’s how it works:
- Suppose an attacker wants to find the plaintext password of a user whose password is hashed using SHA-256. Instead of trying every possible password and hashing each one, the attacker could use a rainbow table that contains precomputed hashes for common passwords like “password123”, “admin”, “welcome”, etc. The attacker can quickly look up the hash and, if found, recover the original password.
Some common defenses include:
- Salting Passwords: Adding a unique salt to each password before hashing prevents the use of rainbow tables.
- Using Strong Hashing Algorithms: Algorithms like bcrypt , scrypt, or Argon2 are designed to be slow and resource-intensive, making rainbow tables less effective.
- Enforcing Strong Password Policies: Encouraging users to create long and complex passwords reduces the chances of the password being found in a precomputed table
How to Protect Against Brute Force Attacks
While we are explain brute force attack is a serious threat, there are several measures you can take to protect your accounts and systems:
- Use Strong Passwords
A strong password is your first line of defense. Avoid using obvious, easily guessable passwords like “123456” or “password.” Instead, use a combination of uppercase and lowercase letters, numbers, and special characters. A password length of at least 12 characters is recommended. - Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security. Even if an attacker manages to crack your password, they will still need access to your second factor, such as a code sent to your phone or generated by an authentication app. - Account Lockout Mechanisms
Many systems allow you to set up account lockouts after a certain number of failed login attempts. This makes it harder for attackers to continue their brute force attack indefinitely. - Use CAPTCHA or ReCAPTCHA
CAPTCHA systems require users to complete a challenge (e.g., identifying images or typing distorted text) before accessing a login form. This helps to block automated tools used explain brute force attack. - Monitor and Detect Suspicious Activity
Regularly monitor login attempts to detect unusual behavior, such as multiple failed logins from the same IP address. Intrusion detection systems (IDS) can be set up to alert administrators of suspicious activity. - Password Managers
Using a password manager can help you generate and store complex, unique passwords for each account. This reduces the temptation to reuse weak passwords across multiple sites. - Limit Login Attempts
Limit the number of login attempts from a specific IP address within a short period. This can help prevent automated attacks from trying unlimited password combinations.
Conclusion
explain brute force attack are a real and ongoing threat, but with the right strategies in place, you can protect your accounts and systems. By using strong passwords, enabling two-factor authentication, and setting up account lockouts, you can significantly reduce the risk of falling victim to these attacks. As always, staying vigilant and aware of emerging security threats is key to maintaining your online safety.