How to scan all ports using Nmap-A Step-by-Step Guide
Discover how to scan all ports using Nmap with our step-by-step guide. Master techniques for effective network scanning and enhance your security skills!
What is Nmap?
Nmap is a free and open-source tool primarily designed for scan all ports using Nmap networks. It allows users to discover devices connected to a network, identify open ports, detect the operating systems and services running on those devices, and much more. The tool is widely used for both network inventory management and security testing.
Nmap’s popularity comes from its versatility. It can scan large networks with hundreds or even thousands of devices. It works by sending specific network packets to devices and analyzing the responses, which helps to map out the network and identify vulnerabilities.
Key Features of Nmap
- Host Discovery: Nmap can identify which devices are live and active on a network. It can even pinpoint hosts that are hidden behind firewalls or Network Address Translation (NAT) devices.
- Port Scanning: One of Nmap’s most important features is its ability to scan all ports using Nmap ports on a target system. It can detect open ports and identify services running on them, which is crucial for both network administration and vulnerability scanning.
- Service and Version Detection: Nmap can probe open ports to detect the services running behind them (e.g., HTTP, SSH, FTP) and even identify the specific version of the service, which can be useful for vulnerability assessment.
- Operating System Detection: By analyzing network responses, Nmap can often determine the underlying operating system (OS) of a device, whether it’s Windows, Linux, macOS, or another OS.
- Scriptable Interface: Nmap features a scripting engine known as NSE (Nmap Scripting Engine), which allows users to write scripts to automate scanning tasks or conduct more complex operations, such as vulnerability scanning.
- Stealth Scanning: Nmap offers various stealth scanning techniques, such as SYN scan and FIN scan, which can be used to bypass basic security defenses or avoid detection by firewalls and intrusion detection systems.
- Comprehensive Output: Nmap generates detailed results that can be saved in multiple formats, including text, XML, and HTML, making it easy for users to interpret and share the findings.
How Does Nmap Work?
Nmap works by sending specially crafted packets to target devices and analyzing the responses. When you run a scan, Nmap sends a request to the target device, like a “ping,” and the device replies if it’s active. If the device is behind a firewall, Nmap can still figure out certain information, depending on the type of scan you’re using.

Nmap uses different types of scan techniques, such as:
- TCP Connect Scan: This is the most basic type of scan. It attempts to establish a full connection (handshake) with the target’s ports. If the connection is established, the port is open.
- SYN Scan: A quicker and more stealthy scan, SYN Scan only sends a “SYN” signal to initiate a connection. If the port responds with a “SYN-ACK,” the port is open.
- UDP Scan: This type scans for open UDP ports, as opposed to TCP ports. UDP is a connectionless protocol, so detecting open UDP ports can be a bit trickier.
- FIN Scan: This scan sends a “FIN” packet to the target, which is typically used to end a connection. Open ports will respond differently than closed ports, making this a more stealthy option.
Common Use Cases-scan all ports using Nmap
- Network Inventory: Nmap can be used by network administrators to map out the devices on a network. This is useful for ensuring that no unauthorized devices are connected.
- Security Auditing: Penetration testers and ethical hackers use Nmap to scan networks for vulnerabilities, open ports, and insecure services. By identifying potential attack vectors, they can help secure a network before attackers find them.
- Firewall Configuration: Administrators can use Nmap to verify whether their firewall rules are correctly configured and whether unauthorized access is possible.
- Malware Detection: Nmap can help identify unusual behavior, such as unexpected open ports or strange services running on a device, which could indicate malware infections.
- System Performance Monitoring: By scanning your network periodically, you can ensure that all services and devices are functioning properly and that there are no network issues that could affect performance.
Installing Nmap on Windows
- Download the Installer:
- Go to the Nmap download page.
- Click on the link for the Windows installer (usually labeled as “Nmap-<version>-setup.exe”).
- Run the Installer:
- Locate the downloaded
.exefile (usually in your Downloads folder). - Double-click the file to run the installer.
- Locate the downloaded
- Follow the Installation Wizard:
- Click “Next” on the welcome screen.
- Accept the license agreement and click “Next”.
- Choose the installation directory (the default is usually fine) and click “Next”.
- Select the components you want to install (the default options are recommended) and click “Next”.
- Choose whether to create a desktop icon and click “Next”.
- Click “Install” to begin the installation.
- Complete the Installation:
- Once the installation is complete, click “Finish” to exit the installer.
- Verify Installation:
- Open Command Prompt (search for “cmd” in the Start menu).
- Type
nmap -vand press Enter. You should see the version of Nmap installed.
Installing Nmap on Linux
The installation process may vary slightly depending on your Linux distribution. Below are instructions for some popular distributions.
For Ubuntu/Debian-based Systems:
- Open Terminal:
- You can usually find it in your applications menu or by pressing
Ctrl + Alt + T.
- You can usually find it in your applications menu or by pressing
- Update Package List:
sudo apt update - Install Nmap:
sudo apt install nmap - Verify Installation:
nmap -v - You can download or clone from github: by this command git clone https://github.com/nmap/nmap.git
For Fedora:
- Open Terminal.
- Install Nmap:
sudo dnf install nmap - Verify Installation:
nmap -v
For Arch Linux:
- Open Terminal.
- Install Nmap:
sudo pacman -S nmap - Verify Installation:
nmap -v
scan all ports using -Nmap
scan all ports using Nmap is relatively straightforward, but it requires a basic understanding of command-line interfaces. Here are some common commands and their functionalities:
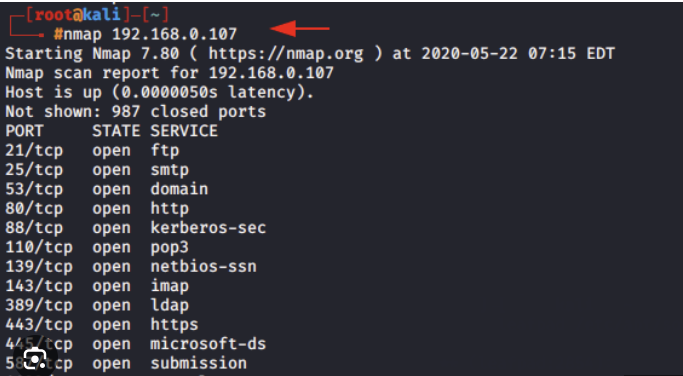
Basic Scanning
To perform a simple scan of a target IP address or hostname, you can use the following command to scan all ports using Nmap
nmap 192.168.1.1
Scanning Multiple Targets
You can scan multiple IP addresses or a range of addresses by specifying them in a comma-separated list or using CIDR notation:
nmap 192.168.1.1,192.168.1.2 2nmap 192.168.1.0/24
Port Scanning
To scan for specific ports, you can use the -p option:
nmap -p- 192.168.1.1
Using the Nmap Scripting Engine
Nmap’s scripting engine allows for more advanced scans. For example, to run a specific script, you can use the --script option:
nmap –script http-vuln* 192.168.1.1
Conclusion
Nmap is an incredibly versatile and powerful tool in the world of network security. Whether you’re a network administrator conducting routine maintenance or a security professional performing penetration tests, Nmap offers valuable insights into the state of your network. With its ability to discover hosts, map open ports, detect services and vulnerabilities, and perform operating system