Database Security- Simple Tips to Keep Your Database Safe
Learn key strategies for Database Security to protect your data from threats and ensure safe, compliant Database Security.
Why is Database Security Important?
- Protection of Sensitive Information: Databases often store sensitive information such as personal identification details, financial records, and proprietary business data. A breach can lead to identity theft, financial fraud, and loss of competitive advantage.
- Regulatory Compliance: Many industries are subject to strict regulations regarding data protection, such as GDPR, HIPAA, and PCI DSS. Non-compliance can result in hefty fines and legal consequences.
- Maintaining Trust: Customers and clients expect organizations to protect their data. A data breach can erode trust and damage relationships, leading to loss of business.
- Preventing Financial Loss: The financial impact of a data breach can be significant, including costs related to remediation, legal fees, and potential lawsuits.
1. Authentication and Authorization
Authentication
Authentication is the process of verifying the identity of users or systems attempting to access the database. It ensures that only authorized individuals or applications can access the database. This is commonly done by requiring users to provide a unique identifier (like a username) along with a secret (such as a password). Stronger authentication methods, such as multi-factor authentication (MFA), add another layer of protection by requiring additional verification beyond just the password.
There are several forms of authentication:
- Password-Based Authentication: Users must provide a password to gain access. However, this can be vulnerable to attacks if passwords are weak or reused.
- Biometric Authentication: Fingerprints or facial recognition systems can be employed for more secure authentication.
- Two-Factor Authentication (2FA): Users need to provide two forms of authentication (e.g., password and a text message code).
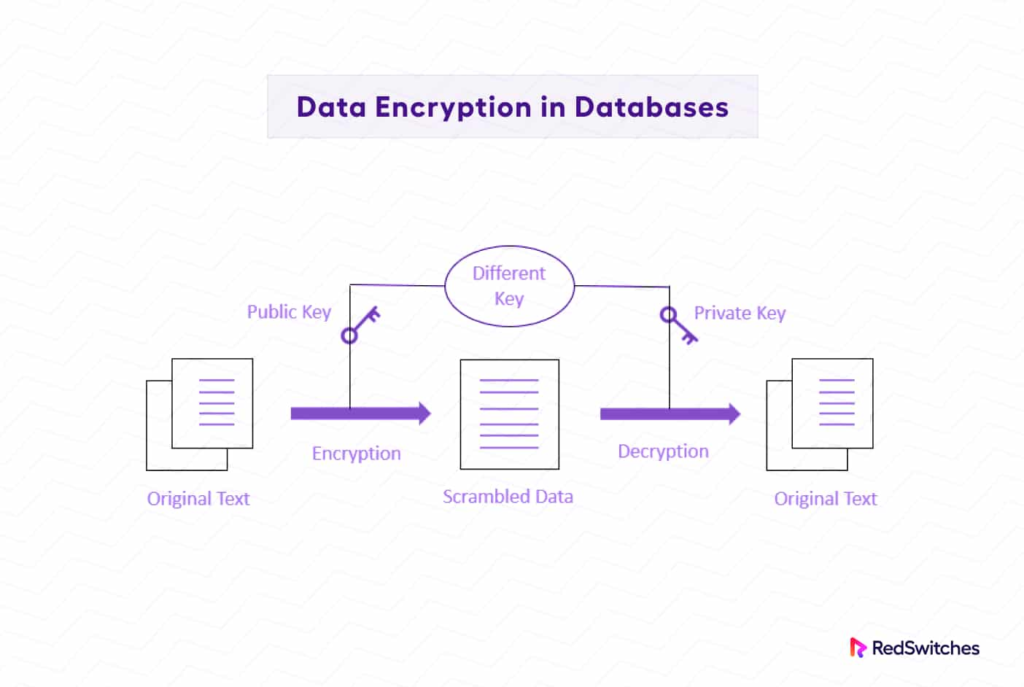
2. Encryption
Encryption is one of the most important aspects of database security. It transforms readable data into an unreadable format, ensuring that unauthorized users or systems cannot access sensitive information, even if they manage to breach the database system. Encryption works at both the storage (at rest) and transmission (in transit) levels.
- Data at Rest Encryption: Data stored on physical disks or in cloud environments is encrypted using algorithms such as AES (Advanced Encryption Standard). If attackers gain access to the physical storage, they will not be able to read the data without the encryption key.
- Data in Transit Encryption: Encryption also protects data when it is transmitted over networks. SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols are commonly used to secure the transmission of data between the database and clients, ensuring that any intercepted data remains unreadable.
- Transparent Data Encryption (TDE): This technique encrypts the entire database, including data files, transaction logs, and backups, without requiring changes to the application.
3. Database Auditing and Monitoring
Database auditing and Database Security involves tracking and recording events and activities within the database to detect unauthorized actions and potential security threats. Auditing helps administrators monitor access to sensitive data, user activities, and modifications to database structures.
- Log Auditing: Databases keep detailed logs of who accessed the database, what actions they performed, when they did it, and what data was involved. These logs can be analyzed for suspicious activity such as failed login attempts, privilege escalation, and unauthorized data access.
- Real-Time Monitoring: Modern database security systems use real-time monitoring tools to continuously track activities and identify irregular patterns. Intrusion detection systems (IDS) and security information and event management (SIEM) systems can help in this process by correlating logs and alerting administrators to abnormal behavior.
- Anomaly Detection: Advanced database systems can use machine learning algorithms to detect anomalies in database usage patterns, flagging unusual queries or behavior that might indicate an attack or breach.
4. Database Backup and Recovery
Having a robust backup and recovery plan is crucial for protecting data from accidental loss, corruption, or ransomware attacks. Regular backups allow the restoration of data in case of a disaster or breach. However, backups must be secured to prevent attackers from tampering with or deleting them.
- Encrypted Backups: Backup data should always be encrypted to ensure its protection in the event of unauthorized access.
- Offsite Storage: Backups should be stored in secure, offsite locations, such as cloud storage or remote servers, to avoid data loss in case of physical theft or damage to primary servers.
- Versioning and Incremental Backups: Implementing versioned and incremental backups ensures that you can restore to a specific point in time, minimizing data loss in case of an attack.
- Testing Recovery Plans: Regularly test backup and recovery procedures to ensure they work when needed.
5. Data Masking and Tokenization
Data masking and tokenization are techniques used to obscure sensitive data in non-production environments while maintaining data usability for testing and development purposes.
- Data Masking: This involves replacing sensitive data with fictional data that still maintains the same structure and format. For example, real credit card numbers can be replaced with randomized, but realistic-looking, numbers.
- Tokenization: This replaces sensitive data with a unique identifier (token) that has no value or meaning outside of the database system. The original data is stored in a secure location, separate from the tokenized data.
6. Database Firewall and Intrusion Prevention Systems (IPS)
Database Security firewall monitors and filters traffic going to and from the database server, preventing unauthorized users from accessing or executing harmful queries. These firewalls inspect incoming traffic for malicious requests and block any attempts to exploit database vulnerabilities.
- SQL Injection Protection: Database firewalls can block SQL injection attempts, where attackers inject malicious SQL queries into an input field to manipulate the database.
- Query Validation: By validating SQL queries, database firewalls ensure that only legitimate, well-formed queries are executed.
Intrusion Prevention Systems (IPS) complement firewalls by actively blocking suspicious activities based on predefined threat signatures or behavior patterns.
7. Database Patching and Updating
Database vendors regularly release security patches and updates to fix known vulnerabilities and improve security. Keeping the database software and its components up to date is crucial for preventing attackers from exploiting these weaknesses.
Test Patches in Staging Environments: Before applying patches to a live database, it’s important to test them in staging environments to prevent compatibility issues.
Automated Patching: Some systems offer automated patch management to ensure that the latest security updates are applied without delay.
challenges of database encryption
How Filesystem Level Encryption Works
Filesystem level encryption operates by encrypting the data as it is written to the disk and decrypting it when it is read. This process is typically transparent to users and applications, meaning that they can access and use files without needing to manage encryption keys or perform any additional steps. Here’s how it generally works:
- Encryption Algorithm: FLE uses cryptographic algorithms (such as AES, RSA, or Blowfish) to encrypt data. The choice of algorithm and key length can affect the strength of the encryption.
- Key Management: A unique encryption key is generated and used to encrypt and decrypt the data. Proper key management is crucial; if the key is lost or compromised, the encrypted data may become inaccessible.
- Transparent Operation: Once FLE is enabled, the operating system automatically handles the encryption and decryption processes. Users can read and write files as usual, without needing to be aware of the underlying encryption.
- File and Directory Protection: FLE typically encrypts all files and directories within the specified filesystem, ensuring that all data is protected, including metadata and file attributes.
Benefits of Filesystem Level Encryption
- Data Protection: FLE provides a robust layer of protection for sensitive data, making it difficult for unauthorized users to access or read the information stored on the filesystem.
- Compliance: Many industries are subject to regulations that require the protection of sensitive data (e.g., HIPAA, GDPR). FLE can help organizations meet these compliance requirements.
- Ease of Use: Since FLE operates transparently, users do not need to change their workflows or manage encryption manually. This ease of use encourages adoption and helps ensure that sensitive data is consistently protected.
- Protection Against Physical Theft: If a device is lost or stolen, FLE can prevent unauthorized access to the data stored on it. Even if an attacker gains physical access to the storage device, they will not be able to read the encrypted data without the encryption key.
- Performance: Modern FLE solutions are designed to minimize performance impacts. Many operating systems and storage devices support hardware acceleration for encryption, allowing for efficient processing without significant slowdowns.
Challenges of Filesystem Level Encryption
- Key Management: Effective key management is critical for FLE. If encryption keys are lost, the encrypted data may become irretrievable. Organizations must implement secure key storage and management practices.
- Performance Overhead: While many FLE solutions are optimized for performance, there can still be some overhead associated with encryption and decryption processes, particularly on older hardware.
- Limited Scope: FLE typically protects data at the filesystem level, which means that data stored in applications or databases may not be encrypted unless those applications also support encryption.
- Potential for Misconfiguration: Improper configuration of FLE can lead to vulnerabilities. Organizations must ensure that encryption is correctly implemented and that all sensitive data is adequately protected.
- Backup and Recovery: Organizations must consider how FLE affects backup and recovery processes. Encrypted data may require special handling during backups to ensure that it can be restored properly.
Implementing Filesystem Level Encryption
To implement filesystem level encryption effectively, organizations should follow these best practices:
- Choose the Right Solution: Select a filesystem level encryption solution that meets your organization’s needs. Consider factors such as compatibility, performance, and ease of use.
- Establish Key Management Policies: Develop and implement policies for key generation, storage, rotation, and revocation. Ensure that keys are stored securely and are accessible only to authorized personnel.
- Train Employees: Educate employees about the importance of data security and the role of filesystem level encryption. Ensure they understand how to use the encryption solution and the implications of losing encryption keys.
- Regularly Audit and Monitor: Conduct regular audits of your encryption implementation to ensure compliance with policies and regulations. Monitor access to encrypted data to detect any unauthorized attempts.
- Test Backup and Recovery Procedures: Regularly test backup and recovery procedures to ensure that encrypted data can be restored successfully. This is crucial for maintaining data availability in case of loss or corruption.






One Comment